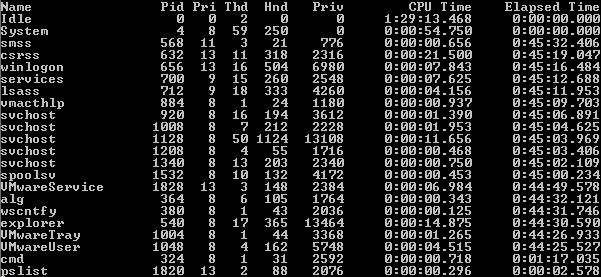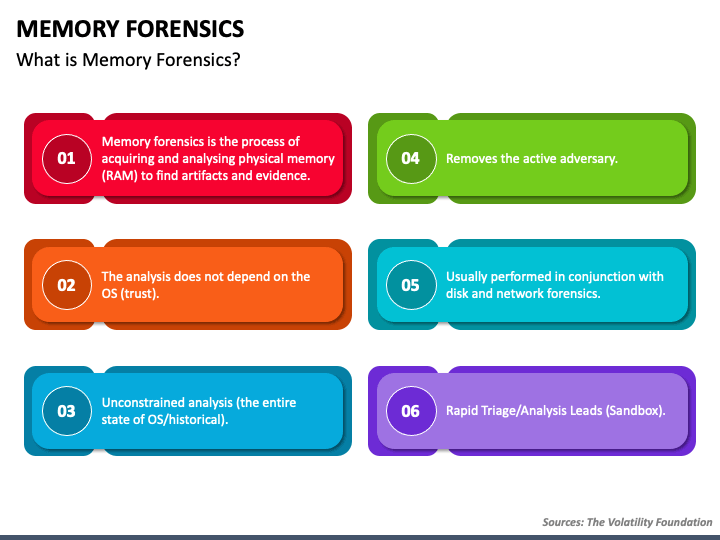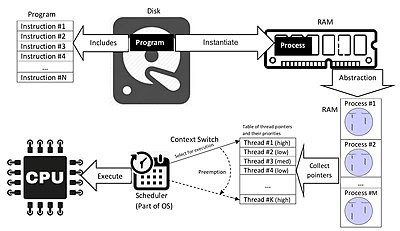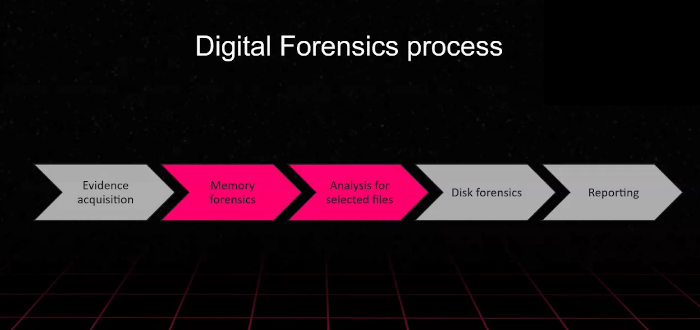
Digging up memories – a deep-dive into memory forensics in the Cyber Security Essentials meetup | Nixu Cybersecurity.
Digging up memories – a deep-dive into memory forensics in the Cyber Security Essentials meetup | Nixu Cybersecurity.

Practical Memory Forensics: Jumpstart effective forensic analysis of volatile memory: Ostrovskaya, Svetlana, Skulkin, Oleg: 9781801070331: Amazon.com: Books

Signature based volatile memory forensics: a detection based approach for analyzing sophisticated cyber attacks | SpringerLink

The Art of Memory Forensics: Detecting Malware and Threats in Windows, Linux, and Mac Memory | Wiley